v
FILE
TYPES:
o A
common technique for implementing file types is to include the type as the part
of the file name.
o The
name is split into two parts- a name and an extension usually separated by
period character.
o In
this way the user and the OS can tell from the name alone what the type of a
file is.
o For
example in MS-DOS a name can consist of up to 8 characters followed by a period
and terminated by an extension of up to 3 characters.
o The
system uses the extension to indicate the type of the file and the type of
operations that can be done on that file. For instance only the files with .com,
.exe or .bat extension can be executed.
o MS-DOS
recognizes only few extensions but application programs also use extensions to
indicate file types in which they are interested. For example, assemblers expect source files
to have .asm extension and the WordPerfect word processor expects its file to
end with .wp extension.
o These
extensions are not required, so a user may specify a file without the extension
an application will look for a file with the given name and the extension it
expects. Because these extensions are
not supported by the OS they can be considered as hints to applications that
operate on them.
v
FILE
ACCESS METHODS:
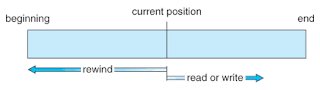
1. Sequential Access:
o The
simplest access method is sequential
access. Information in the file is
processed in order one record after the other. This mode of access is by far
the most common.
o For
example editors and compilers usually access files in this fashion.
o The
bulk of the operations on a file is reads and writes.
o Read
operation reads the next version of the file and automatically advances a file
pointer which tracks the IO location. Similarly
a write appends to the end of the file and advances to the end of the newly
written material.
o Such
a file can be reset to the beginning and on some systems a program able to skip
forward or backward ‘n’ records for some integer n where n=1 usually.
(Sequential
access file)
2. Direct Access:
o Another
method is Direct Access or relative access.
If file is made up of fixed length logical records that allow programs
to read and write records rapidly in no particular order.
o The
Direct Access method is based on a disc model of a file, since disc allow
random access to any file block. For
Direct Access, file is viewed as a numbered sequence of blocks or records and Direct
Access file allows arbitrary blocks to be read or written.
o Thus
we may read block 14, then read block 53 and then write block 7. There are no restrictions on the order of
reading or writing for a Direct Access file.
o Direct
Access files are of great use for immediate access to large amounts of
information. Data bases are often of
this type.
o For
Direct Access method the file operations must be modified to include the block
number as a parameter. The block number
provided by the user to the OS is normally a relative block number.
o A
relative block number is an index relative to the beginning of the file. The use of relative block numbers allows the
OS to decide where the file should be placed and helps to prevent the user from
accessing portions of the file system that may not be part of his file.
o Some
systems start their relative block numbers at 0 while others start at 1. Not all OS support both sequential and Direct
Access for files. Some systems allow
only sequential file access while others allow only Direct Access.
o Some
systems require that if it been defined as sequential or a direct when it is
created; such a file can be assessed only in a manner consistent with its
declaration.
3. Other Access Methods:
o Other
access methods can be built on top of a Direct Access method. This method is generally involves the
construction of an index for the file.
o The
index like an index in the back of a book contains pointers to various
blocks. To find a record in the file we
first search the index and then use the pointer to access the file directly and
to find the desired record.
o The
structure allows us to search a large file doing little IO. With large files, the index file itself may
become too large to be kept in memory.
o One
solution is to create an index for the index file. The primary index file would contain pointers
to secondary index files which would point to the actual data items.
o For
example IBM’s Indexed Sequential Access
Method (ISAM) uses a small master index that points to a disc blocks of
secondary index. The secondary index
blocks points to the actual file blocks.

No comments:
Post a Comment