Memory Management Requirements:
There are so
many methods, policies for memory management. To observe these methods suggest
five requirements.
- Relocation
- Protection
- Sharing
- Logical organization
- Physical organization
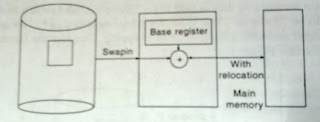
1. Relocation:
Relocation is a mechanism to convert the logical address into
physical address. An address generated by CPU is said to be logical address and
an address generated by Memory Manager is said to be physical address.
Physical address = Contents of Relocation Register + Logical
Address
Relocation is necessary at the time of swap in a process from
one backing store to main memory. Almost all times, the process occupies the
same location at the time of swap in. But, sometimes it is not possible; as
such the relocation is required. Consider the following fig:
Fig: Relocation
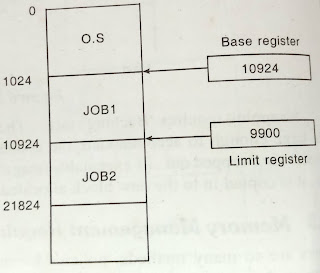
2. Protection:
The word protection means provide security from unauthorized
usage of memory. An OS can protect the memory with the help of a base and limit registers. Base registers consist of the
starting address of the next process. The Limit registers specifies the
boundary of that job. The Limit register is also said to be fencing register. Consider the
following fig:
Fig: Main Memory Protection
The base register holds the smallest legal physical memory address;
the limit register contains the size of the process. Consider the below figure.
It depicts the hardware protection mechanism with base and limit registers.
Fig: Memory protection with Base and
Limit
If the logical address is greater than the contents of a base register, it is authorized access, otherwise; it is a trap to operating system. If the physical address (logical + base) is less than the base limit, it causes no problems; otherwise it is a trap to the operating system.
3. Sharing:
Generally, protection mechanisms are required at the time of
access to the same portion of main memory by several processes. Accessing the same portion of main memory
by a number of processes is said to be “sharing”. Suppose, to say if number of processes are executing
same program, it is advantageous to allow each process to access same copy of
the program rather than it having its own copy. If each process maintains a
separate copy of that program, a lot of main memory will be wasted.
For ex: 3 users want to take their resumes using word
processor. Then the 3 users share the word processor in the server; in the
place of individual copy of word processor. Consider the following fig. that
depicts the sharing of word processor.
Fig: Memory sharing
4. Logical Organization:
We know that main memory in a computer system is organized as
a linear or one dimensional address space that consists of a sequence of bytes
or words. Secondary memory, at its physical level, is similarly organized. Although
this organization closely mirrors the actual machine hardware, it does not
correspond to the way in which programs are typically constructed.
Most programs are organized into modules, some of which are modifiable
(read only, execute only) and some of which contain data that may be modified. If
the operating system and computer hardware can effectively deal with user
programs and data in the form of modules of some sort, then a number of
advantages can be realized.
5. Physical
Organization:
A computer memory is organized into at least two levels: main
memory and secondary memory. Main memory provides fast access at a relatively
high cost. In addition, main memory is volatile i.e. it does not provide
permanent storage. Secondary memory is slower and cheaper than main memory and
it is usually not volatile. Thus, secondary memory of large capacity can be
provided to allow for long-term storage of programs and data, while a smaller
main memory holds programs and data currently in use.


No comments:
Post a Comment